Dear dkosovic, thank you once again for your continued effort to help me resolve this issue. I followed your instructions and here’s the outcome:
Issue 1 - No GUI VPN password prompt
Thank you, though I haven’t tried this for now, as it is moot if I can’t make the VPN work.
Issue 2 - Broken routing
The local and the remote LAN use different subnets. This is confirmed by the outcome of the $ ip route command below. I didn’t use netstat, because Lubuntu said it wasn’t installed and I didn’t want to bring additional variables to the problem by installing additional software.
STEP 1: Checking the version of network-manager-l2tp:
user@user-virtualbox:~$ dpkg -l network-manager-l2tp
Desired=Unknown/Install/Remove/Purge/Hold
| Status=Not/Inst/Conf-files/Unpacked/halF-conf/Half-inst/trig-aWait/Trig-pend
|/ Err?=(none)/Reinst-required (Status,Err: uppercase=bad)
||/ Name Version Architecture Description
+++-====================-=============================-============-======================================>
ii network-manager-l2tp 1.20.8-1~ubuntu22.04.1~ppa1.1 amd64 network management framework (L2TP plu>
lines 1-6/6 (END)
STEP 2: Checking the routing without the VPN:
user@user-virtualbox:~$ sudo ip route
[sudo] password for user:
default via 192.168.8.1 dev enp0s3 proto dhcp metric 100
192.168.8.0/24 dev enp0s3 proto kernel scope link src 192.168.8.210 metric 100
user@user-virtualbox:~$
Confirmation that the VPN is down:
ip add show dev ppp0
user@user-virtualbox:~$ sudo ip add show dev ppp0
[sudo] password for user:
Device "ppp0" does not exist.
user@user-virtualbox:~$
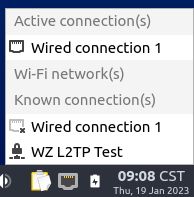
STEP 3: Connecting to the VPN:
user@user-virtualbox:~$ nmcli con up id 'WZ L2TP Test' --ask
You need to authenticate to access the Virtual Private Network “WZ L2TP Test”.
Password (vpn.secrets.password): •••••••••••
You need to authenticate to access the Virtual Private Network “WZ L2TP Test”.
Pre-shared key (PSK) (vpn.secrets.ipsec-psk): •••••••••••
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/3)
user@user-virtualbox:~$
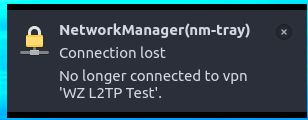
After even the GUI notification showed that the VPN was up, I ran:
user@user-virtualbox:~$ sudo ip route
default dev ppp0 proto static scope link metric 50
default via 192.168.8.1 dev enp0s3 proto dhcp metric 100
24.xxx.xxx.168 dev ppp0 proto kernel scope link src 192.168.70.200
24.xxx.xxx.168 via 192.168.8.1 dev enp0s3 proto static metric 50
24.xxx.xxx.168 dev ppp0 proto kernel scope link src 192.168.70.200 metric 50
192.168.8.0/24 dev enp0s3 proto kernel scope link src 192.168.8.210 metric 100
192.168.8.1 dev enp0s3 proto static scope link metric 50
user@user-virtualbox:~$
and
user@user-virtualbox:~$ sudo ip add show dev ppp0
5: ppp0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1400 qdisc fq_codel state UNKNOWN group default qlen 3
link/ppp
inet 192.168.70.200 peer 24.xxx.xxx.168/32 scope global ppp0
valid_lft forever preferred_lft forever
user@user-virtualbox:~$
Ping to the LAN side of the router (through the VPN) didn’t go through:
user@user-virtualbox:~$ sudo ping 192.168.70.1
PING 192.168.70.1 (192.168.70.1) 56(84) bytes of data.
^C
--- 192.168.70.1 ping statistics ---
36 packets transmitted, 0 received, 100% packet loss, time 36041ms
Ping to Google did - but only after the VPN connection dropped, as evident from the number of sent/lost packets:
user@user-virtualbox:~$ sudo ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=31 ttl=118 time=114 ms
64 bytes from 8.8.8.8: icmp_seq=32 ttl=118 time=117 ms
64 bytes from 8.8.8.8: icmp_seq=33 ttl=118 time=122 ms
64 bytes from 8.8.8.8: icmp_seq=34 ttl=118 time=115 ms
64 bytes from 8.8.8.8: icmp_seq=35 ttl=118 time=117 ms
^C
--- 8.8.8.8 ping statistics ---
35 packets transmitted, 5 received, 85.7143% packet loss, time 34727ms
rtt min/avg/max/mdev = 114.453/116.940/121.660/2.638 ms
user@user-virtualbox:~$
As for the Lubuntu log, if you give me an idea what to look for, I’ll paste that particular section here.
I apologize for only experimenting with the connection on weekends. Starting later this week, I’ll be in the position to follow your instructions within 24 hours.
Thank you very much!